Oh, good thing it's only "root". You had me worried there for a second :). Interestingly, there was a somewhat similar Cisco advisory one year ago (on CUCDM) where also a default SSH key was present, and equally led to root privileges. Searching for "default credentials" on Cisco's advisory web site shows that for the past several years, the presence of backdoor and default users continues to be a recurring issue:
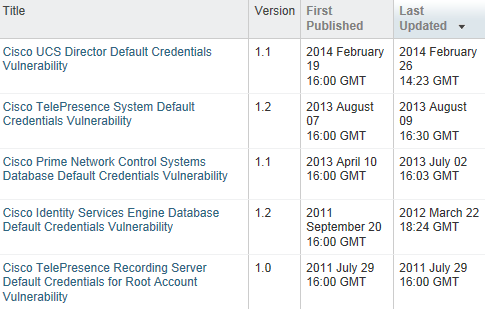
To Cisco's credit, they seem to have found today's SSH key problem on their own, before it was abused, so maybe this is a sign of better times to come, and evidence that after all these years, someone at Cisco has actually started to systematically audit their entire code base for the presence of default credentials. Or maybe it just was a lucky find, and the "stellar" 10 year track record of default credential security bulletins will continue for another decade? Time will tell...
'취약점 정보1' 카테고리의 다른 글
| Adobe Flash Player 신규 취약점 보안 업데이트 권고 (0) | 2015.07.11 |
|---|---|
| OpenSSL 취약점 보안업데이트 권고 (0) | 2015.07.11 |
| Updates to OpenSSL fix vulnerabilities related to Logjam (0) | 2015.06.17 |
| Samsung Galaxy S phones fail to properly validate Swiftkey language pack updates (0) | 2015.06.17 |
| 블루코트 ssl취약점 (0) | 2015.06.02 |