Honeypots offer a powerful and exciting way of learning about attackers’ presence and methods. They contribute towards a security program that incorporates deception. However, honeypots can be tricky to set up and oversee. The open-source tool Modern Honey Network (MHN) by ThreatStream drastically simplifies the tasks of installing and managing low-interaction honeypots. Armed with MHN and access to an inexpensive public cloud provider, anyone can start experimenting with and learning from honeypots.
Deploying Honeypots Using MHN
A key component of the Modern Honey Network is an easy-to-use web application called MHN Server. I’ll explain how to easily install this software below. First, let me show you why it might be worth your while to set it up. The MHN Server app, once installed per instructions below, makes it very convenient to deploy honeypots to other systems:
![]()
The application lets you select the desired honeypot, such as Wordpot, Kippo, Dionaea, Shockpot, etc. It then generates a one-line Linux command that you will run on the system that will host the honeypot. The command will install all the necessary dependencies along with the honeypot software and link the sensor to the MHN Server, so you can observe and control the honeypot from a central location:
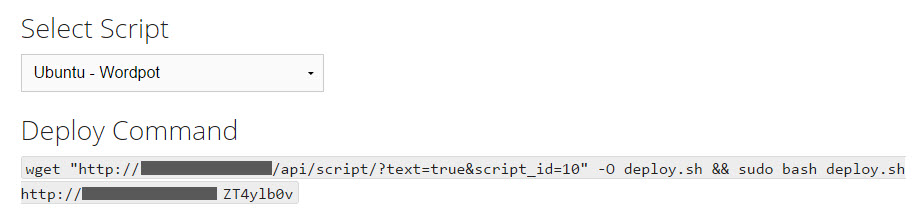
A convenient way of starting to experiment with honeypots and MHN is to activate one or more inexpensive Linux systems at public cloud provider such as DigitalOcean (the link includes my referral code). I like this provider in part because it offers a low-end virtual private server instance for as little as $5 per month. You can deploy a “droplet” running Ubuntu there in a few clicks:
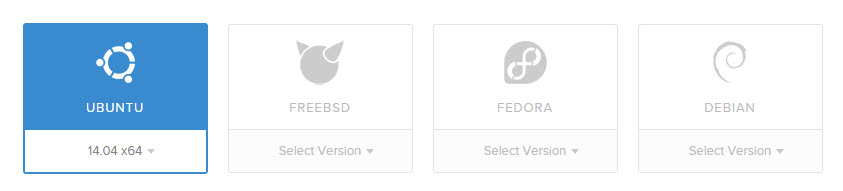
Once the new system is active, log into it and simply run the one-line command generated by MHN Server.
Installing MHN Server
Prior to deploying and managing honeypots using the Modern Honey Network, you need to install MHN Server software on an Internet-accessible Linux box. Consider setting up a dedicated Ubuntu system for this purpose using a cloud hosting provider as explained above.
After logging into the newly-created system, follow MHN instructions for installing its server application. Essentially, you’ll need to run the following commands as “root”:
cd /opt/ apt-get install git -y git clone https://github.com/threatstream/mhn.git cd mhn/scripts/ ./install_hpfeeds.sh ./install_mnemosyne.sh ./install_honeymap.sh
You’ll be prompted for a few configuration parameters, including the desired username and password. Once the installation completes, you can connect to MHN Server by directing your browser to the server’s IP address or hostname over HTTP, at which point you’ll have the opportunity to log in.
If you expect to keep the server after completing your experiments, be sure to harden its configuration. This applies to the systems where your honeypots run as well.
Centrally Monitoring Your Honeypots
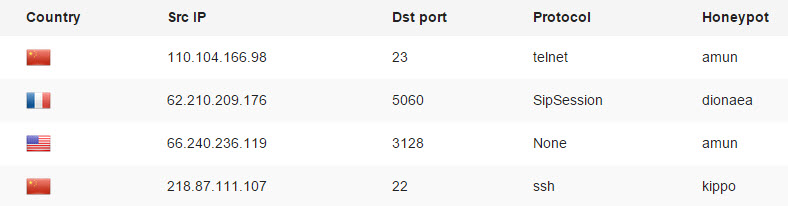
MHN Server gives you the ability to centrally observe the data captured by the honeypots you may have deployed throughout the world. For instance, web application conveniently displays the IP addressing of the attacking systems, along with the details about the targeted protocol:
The application offers other views, such as the one outlining the top 5 attacking IPs seen by your honeypot network:

Start Experimenting, See What You Learn
As you can see, the Modern Honeypot Network tool makes it convenient and painless to deploy a variety of honeypot sensors with minimal expense. If you’d like to start experimenting, deploy two or more low-end servers using your favorite public cloud provider, install MHN Server software on one of them and deploy a few honeypots to others. The data you gather will help you understand attack trends and methods and might inspire you to experiment and learn in other creative ways.
For additional information about the Modern Honeypot Network, watch the brief introduction that its primary author Jason Trost recorded:
To learn more about honeypots and deception, see my earlier articles on this topic:
- Honeypots as Part of a Modern IT Infrastructure
- Specialized Honeypots for SSH, Web and Malware Attacks
- Reflections Upon Deception and Protean Security Tactics
'Security_Study' 카테고리의 다른 글
| DDoS on UPNP Devices (0) | 2015.03.17 |
|---|---|
| No Wireshark? No TCPDump? No Problem! (0) | 2015.03.05 |
| Exploiting UEFI boot script table vulnerability (0) | 2015.02.09 |
| SQL Injection Cheat Sheet (0) | 2015.01.27 |
| Session Hijacking Cheat Sheet (0) | 2015.01.27 |