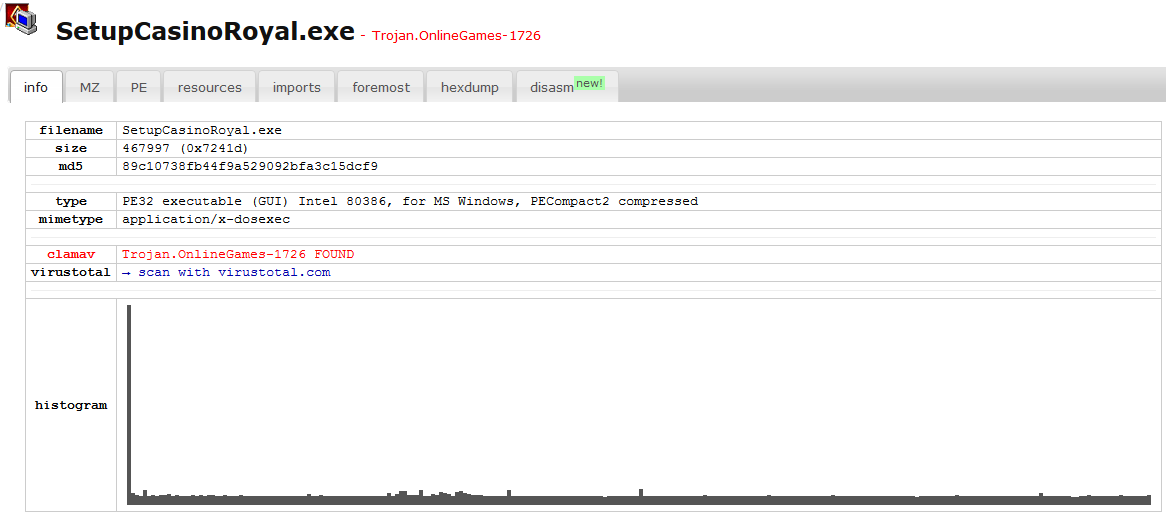
re you looking for a tool to analyze Windows Portable Executable (PE) files? Consider using pedump a ruby win32 PE binary file analyzer. It currently support DOS MZ EXE, win16 NE and win32/64 PE.
There are several ways to install the ruby package; however, the simplest way is to execute "gem install pedump" from a Linux workstation. You can also download the file here or use the pedumpwebsite to upload your file for analysis. This example shows the output from the pedump website.
You can obtain the same results as this output with the command line version by executing "pedump --all SetupCasinoRoyal.exe".
The command line version doesn't currently have foremost, hexdump or the disassembler function. However, you can get the same hexdump output by executing "hexdump -C SetupCasinoRoyal.exe" from your Unix system.
guy@seeker:~/malware/casino$ hexdump -C SetupCasinoRoyal.exe |more
00000000 4d 5a 90 00 03 00 00 00 04 00 00 00 ff ff 00 00 |MZ..............|
00000010 b8 00 00 00 00 00 00 00 40 00 00 00 00 00 00 00 |........@.......|
00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000030 00 00 00 00 00 00 00 00 00 00 00 00 10 01 00 00 |................|
00000040 0e 1f ba 0e 00 b4 09 cd 21 b8 01 4c cd 21 54 68 |.............!Th|
00000050 69 73 20 70 72 6f 67 72 61 6d 20 63 61 6e 6e 6f |is program canno|
00000060 74 20 62 65 20 72 75 6e 20 69 6e 20 44 4f 53 20 |t be run in DOS |
00000070 6d 6f 64 65 2e 0d 0d 0a 24 00 00 00 00 00 00 00 |mode....$.......|
This tool provides an easy way to dump headers, find packers and resources used by exe and dll, in the end providing a quick look inside suspicious PE file.
[1] http://pedump.me/
[2] http://pedump.me/89c10738fb44f9a529092bfa3c15dcf9/#resources
[3] https://github.com/zed-0xff/pedump
[4] https://rubygems.org/gems/pedump
[5] https://github.com/zed-0xff/pedump/archive/master.zip
[6] http://en.wikipedia.org/wiki/Portable_Executable
-----------
'Security_News > 해외보안소식' 카테고리의 다른 글
| 오라클, 윈도 XP용 자바 업데이트 (0) | 2014.07.09 |
|---|---|
| Botnet Advancements – The latest trends in botnet activities (0) | 2014.07.07 |
| 전력망 보안 위협 증가 추세 (0) | 2014.07.05 |
| 美증권거래소, 상장사 대상 사이버 공격 대응여부 조사 (0) | 2014.07.05 |
| NSA XKeyscore 분석결과 토르 사용자 추적 드러나 (0) | 2014.07.05 |