728x90
Operation Windigo: Linux malware campaign that infected 500,000 Computers Worldwide
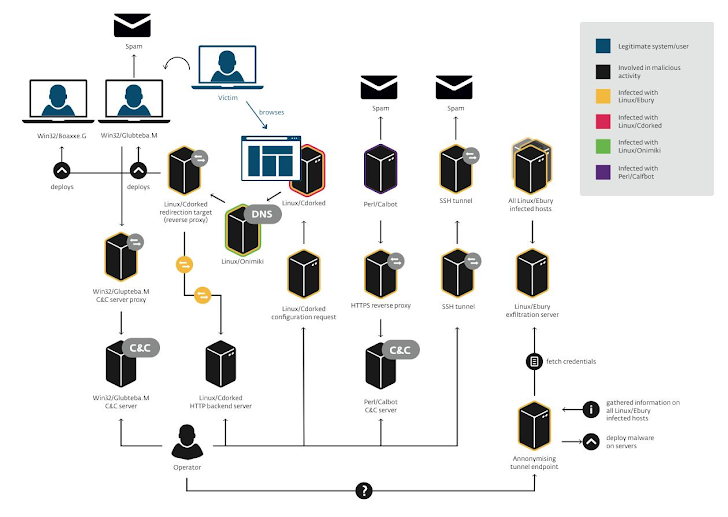
In late 2013, Security Researchers identified thousands of Linux systems around the world infected with the OpenSSH backdoor trojan and credential stealer named Linux/Ebury, that allows unauthorized access of an affected computer to the remote attackers.
Antivirus Firm ESET's Reseacher team has been tracking and investigating the operation behind Linux/Ebury and today team uncovers the details [Report PDF] of a massive, sophisticated and organized malware campaign called 'Operation Windigo', infected more than 500,000 computers and 25,000 dedicated servers.
'We discovered an infrastructure used for malicious activities that is all hosted on compromised servers. We were also able to find a link between different malware components such as Linux/Cdorked, Perl/Calfbot and Win32/Glupteba.M and realized they are all operated by the same group.' ESET reported.
Malware used in Operation Windigo:
- Linux/Ebury – an OpenSSH backdoor used to keep control of the servers and steal credentials.
- Linux/Cdorked – an HTTP backdoor used to redirect web traffic. We also detail the infrastructure deployed to redirect traffic, including a modified DNS server used to resolve arbitrary IP addresses labeled as Linux/Onimiki.
- Perl/Calfbot – a Perl script used to send spam.
The Group behind the attacks may have been active since December 2012, using a modified version ofOpenSSH, an open source alternative to proprietary Secure Shell Software (SSH) to infect thousands of servers and desktop computers, apparently, stole user credentials on system and SSH private keys for outgoing SSH connections.
"According to our analysis, over 25,000 servers have been affected over the last two years. More than 10,000 of them are still infected today." ESET reported, "using the Linux/Ebury OpenSSH backdoor"
Hackers have accessed a wider range of compromised machines, used them to redirect half of a million web visitors to malicious websites and abusing the server bandwidth to send more than 35,000,000 spam messages per day. If victim will use a Smartphone to surf the malicious link from Spam mails, they will be redirected to Porn sites, with the intention of making money.
High-profile Targets: Report listed some affected high profile servers and companies, includingcPanel (famous web hosting control panel) and Linux Foundation’s kernel.org (main repository of source code for the Linux kernel).
ESET Researchers collaborated with CERT-Bund, the European Organization for Nuclear Research (CERN), the Swedish National Infrastructure for Computing and other agencies to fight against this malware campaign.
Affected Operating systems include Linux, FreeBSD, OpenBSD, OS X, and even Windows (with Perl running under Cygwin) and affected countries are US, Germany, France, Italy, Great Britain, Netherlands, Russian Federation, Ukraine, Mexico and Canada.
How to Check, if you have been compromised? If you use only 'ssh -G' command, a clean server will print: 'ssh: illegal option -- G', but an infected server will only print the usage.
Administrators can use the following UNIX/Linux command to check:
$ ssh -G 2>&1 | grep -e illegal -e unknown > /dev/null && echo "System clean" || echo "System infected"If your system or server was also compromised in the same campaign, it's recommended to re-install the system or re-set all passwords and private OpenSSH keys.
728x90
'Security_News > 해외보안소식' 카테고리의 다른 글
| 핵심 인프라 기업을 해킹 - 펜 테스터의보기 (0) | 2014.03.19 |
|---|---|
| 사이버 공격이 산업의 증가 대상으로하지만 의료 산업은 여전히 사이버 위협 대비 부족 (0) | 2014.03.19 |
| Google Play Store was crashed twice by a Turkish hacker when he tried to test vulnerability he discovered on the Android apps publishing system, known as Google's Developer Console. (0) | 2014.03.19 |
| 미국, ICANN 통제권 이양 (0) | 2014.03.19 |
| 애플 iOS7 PRNG 이전버전보다 취약 (0) | 2014.03.19 |