As mentioned in my previous blog post this afternoon, it appears Microsoft has added back the ability to dump physical memory to disk (in the form of a dump file) from user mode via NtSystemDebugControl. I wrote a quick proof-of-concept tool and generated what appears to be a 250mb kernel bitmap dump:
Loading Dump File [C:\XXXXXX\dump.dmp]
Kernel Bitmap Dump File: Only kernel address space is available
...
Windows 8 Kernel Version 9600 UP Free x86 compatible
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 9600.16404.x86fre.winblue_gdr.130913-2141
Machine Name:
Kernel base = 0x81062000 PsLoadedModuleList = 0x8125b218
Debug session time: Fri Aug 1 18:40:22.806 2014 (UTC - 4:00)
System Uptime: 0 days 1:50:55.292
Loading Kernel Symbols
...
..
STACK_TEXT:
a489fa88 8129c557 842fa2b0 00000000 868d7e60 nt!MmDuplicateMemory+0x67a
a489fab0 8148d3b2 b4e31030 00000000 a489fb34 nt!IopLiveDumpCaptureMemoryPages+0x39
a489facc 811cb332 00000000 00000000 00000000 nt!IoCaptureLiveDump+0xc9
a489fb1c 814e9324 eb98f881 00000025 00c4fc74 nt!DbgkCaptureLiveKernelDump+0x2f4
a489fbf4 811736f7 00000025 00c4fd60 00000028 nt!NtSystemDebugControl+0x691
a489fbf4 7794f804 00000025 00c4fd60 00000028 nt!KiSystemServicePostCall
WARNING: Frame IP not in any known module. Following frames may be wrong.
00c4fdc0 00000000 00000000 00000000 00000000 0x7794f804
When I ran the tool (as an administrator), I saw this in the attached kernel debugger:
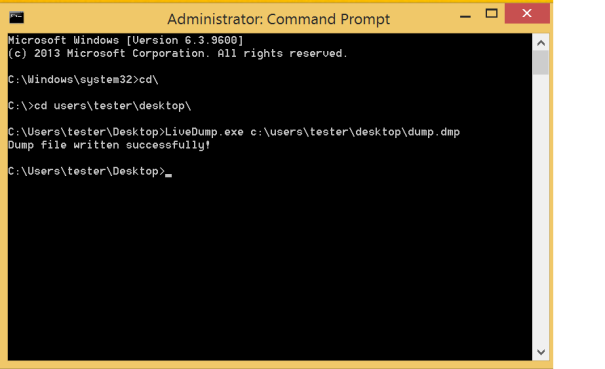
WER/CrashAPI:1959: ERROR ReadProcessMemory failed while trying to read PebBaseAddress
WER/CrashAPI:2068: ERROR Failed to read the peb from the process
'security_downloads' 카테고리의 다른 글
| 모바일 정보 보호 응용 프로그램에서 제공하는 기능을 검증 (0) | 2014.08.09 |
|---|---|
| DDoS and Geopolitics – Attack analysis in the context of the Israeli-Hamas conflict (0) | 2014.08.08 |
| Threats & Indicators: A Security Intelligence Lifecycle (0) | 2014.08.04 |
| Remote code execution on Android devices (0) | 2014.08.03 |
| IM 프로토콜에 대한 Noodling (0) | 2014.07.27 |