728x90
This blog post contains the details of detecting the encrypted Gh0st RAT communication, decrypting it and finding malicious Gh0st Rat artifacts (like process, network connections and DLL) in memory. I also present a Volatility (Advanced Memory Forensics Framework) plugin (ghostrat) which detects the encrypted Gh0st RAT communication, decrypts it and also automatically identifies the malicious Gh0st RAT process, its associated network connections and the loaded DLL's. This can help the digital forensic investigators and incident responders to quickly narrow down on the Gh0st RAT artifacts without having to spend time on the manual investigation.
1. Introduction
Gh0st RAT is a Remote Access Trojan used in many cyber espionage/targeted attacks like "Gh0stnet" which was targeted against compromise of computer systems owned by the Private Office of the Dalai Lama, and several other Tibetan enterprises. Gh0st RAT was also used to attack large corporations in the oil and gas industry dubbed as "Operation Night Dragon" by McAfee. This malware has multiple capabilities which allows the attackers to take control of the infected machine some of them include screen control, keystroke logging, webcam eavesdropping, voice monitoring, and remote file downloads. More details of this malware can be found in this whitepaper titled "Know Your Digital Enemy"
When a host is infected with Gh0st RAT, the malware collects the system information, encrypts the collected information and sends it to the C2 (command and control) server. In this blog I will show how this communication takes place and how this communication can be detected and decrypted in memory using a Volatility plugin.
2. Network Communications of Gh0stRat
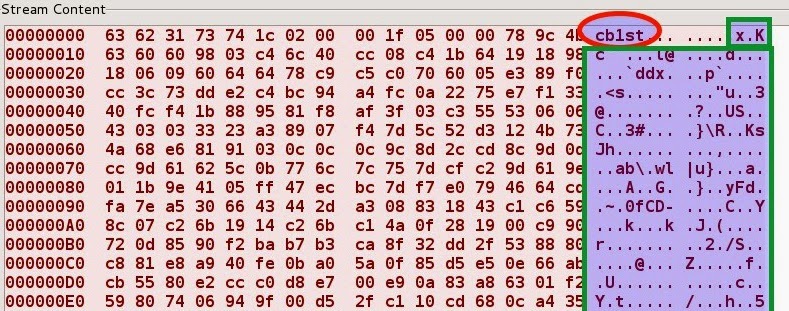
An example of Gh0st RAT traffic communication is shown below, this traffic contains 13 byte header, the first 5 bytes (called the Magic header) is a keyword in clear text like 'Gh0st' and the rest of the bytes are encoded using zlib compression algorithm (marked in green). Different variants use different magic headers and some variants use more than 5 byte magic headers
Below screenshots show variants of Gh0st RAT using different magic headers
3. Why Volatility Plugin?
There exists a Gh0st decode module in "chopshop" which can decrypt the Gh0st RAT communication from the packet capture(pcap), But while Investigating a real incident there exist some challenges like:
a) Organization might not have a full packet capture solution
b) It is not possible to trace back the malicious process even if the packet capture (pcap) is available
c) It is not possible to trace back the malicious DLL using the packet capture
Memory Forensics can help in overcoming these challenges so I decided to write a Volatility plugin which could identify from the memory image the encrypted Gh0st RAT communication, decrypt it and also identify the malicious process, network communications associated with that malicious process and the DLL's loaded by that malicious process. This can help the Investigators and the incident responders to not only decrypt the malicious communication but also to quickly identify the malicious Gh0st RAT artifacts in an automated way.
4. Detecting Gh0st RAT manually using memory image
In this section I show the technique to detect the encrypted Gh0st RAT communication from the memory image manually using Volatility advanced memory forensics framework.
4.1. Detecting Gh0st RAT network communication
Even though the Gh0st RAT variants change the magic keyword, it still follows a pattern in its network communication which can be detected using the regular expression shown below.
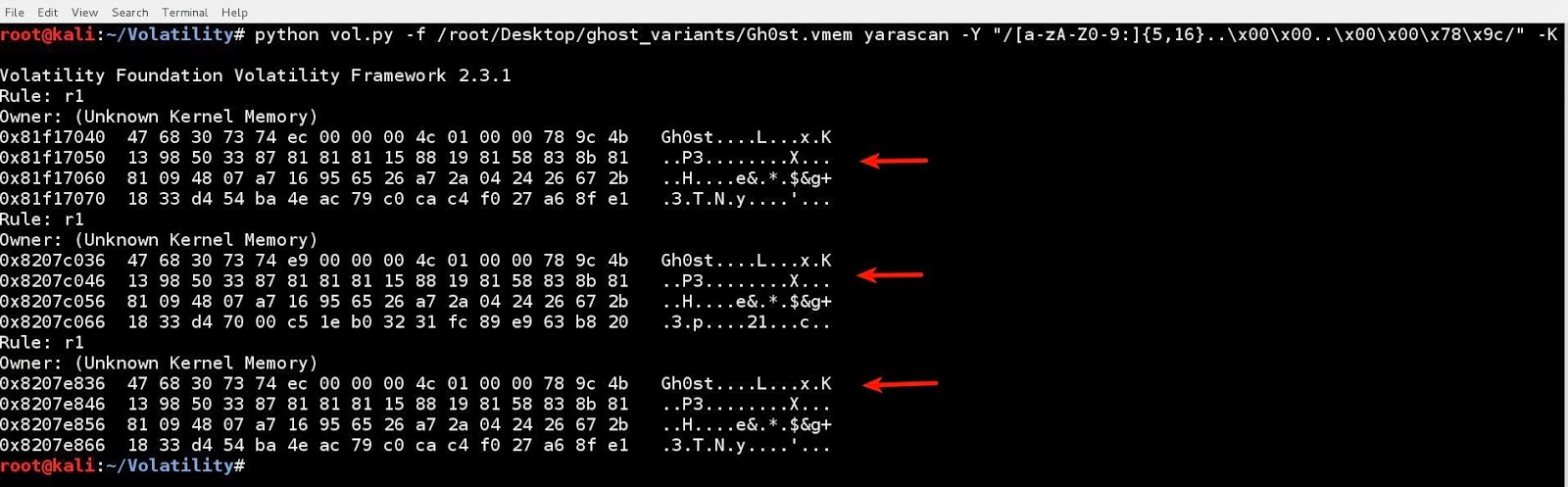
/[a-zA-z0-9:]{5,16}..\x00\x00..\x00\x00\x78\x9c/
In order to detect this pattern in memory, Volatility’s yarascan plugin can be used against the memory image. The below screenshots shows the encrypted traffic detected in kernel memory. Once the encrypted traffic is detected, it can then be decrypted.
4.2. Detecting malicious Gh0st RAT process
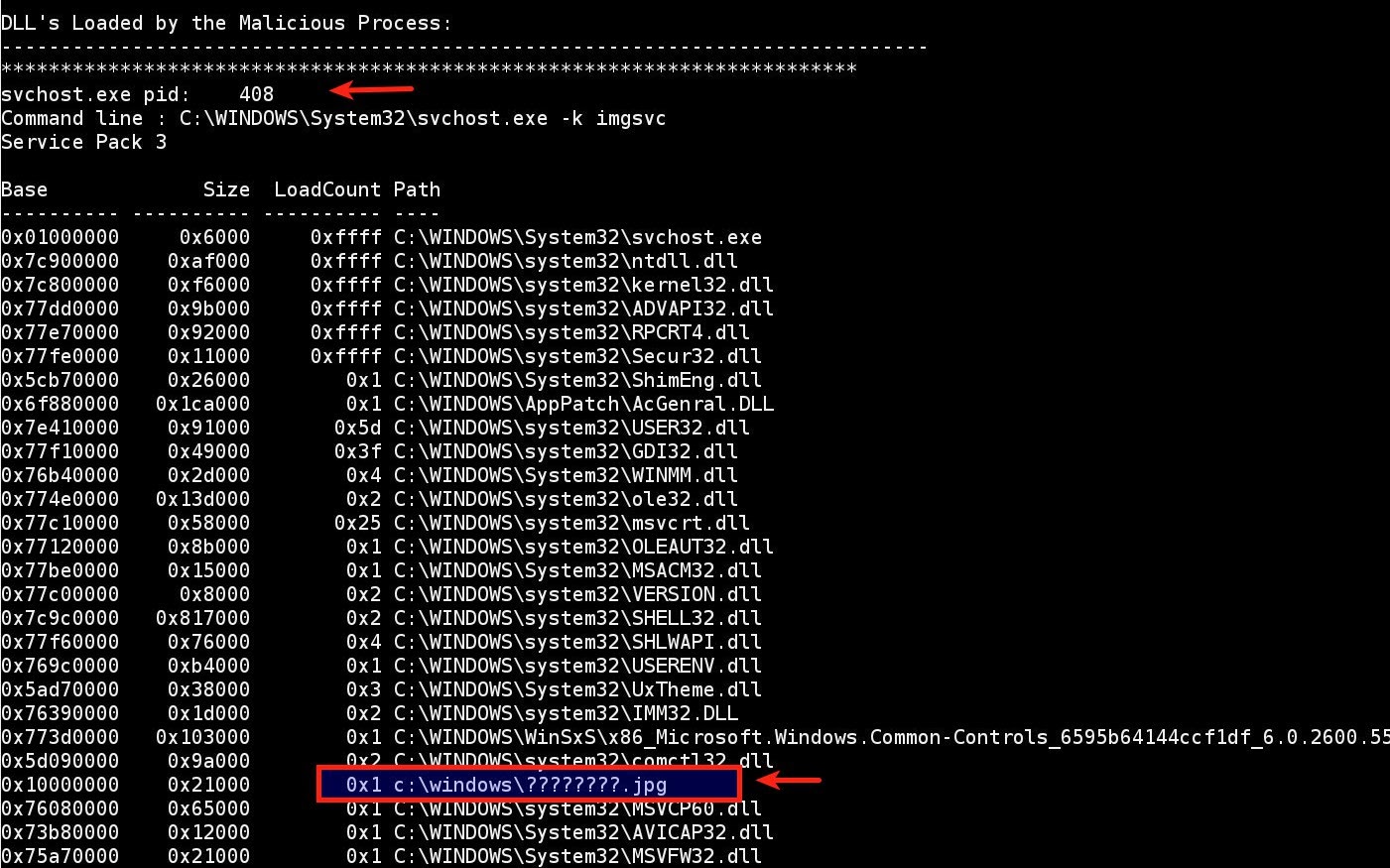
From an incident response perspective it is important to determine the malicious Gh0st RAT process. Once the network traffic is detected in memory, we can get the magic keyword from the network traffic (in this case Gh0st) and then look for the process that contains this magic keyword. The below screenshot shows the process (svchost.exe with pid 408) which contains the magic keyword (Gh0st).
5. Automating Gh0st RAT detection using Volatility plugin
In this section, I present a Volatility plugin (ghostrat), which automates steps mentioned in the section 4 by:
- Looking for the Gh0st RAT network traffic pattern in kernel memory
- Extracting the magic keyword from detected pattern and decrypting the communication.
- Determining the malicious process by searching for the magic keyword in the user process memory
- Determining the network connections made by the malicious process
- Determine the DLL's loaded by the malicious process
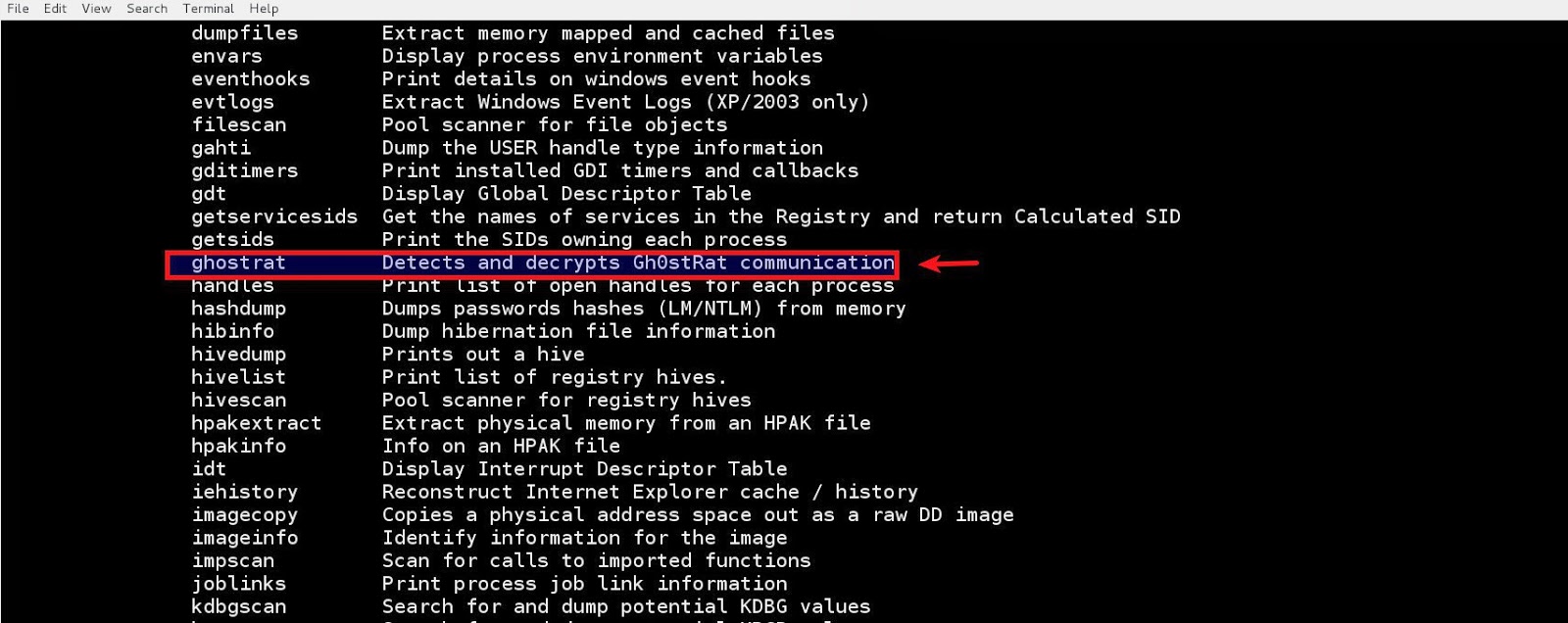
Below screenshot shows the ghostrat Volatility plugin. This plugin can be downloaded from GitHub or from Volatility Plugin Contest 2014.
To use the plugin just copy it to the Volatility plugins directory. After copying the plugin, the Volatility's plugin system will automatically register the plugin as shown below
6. Detecting and decrypting multiple variants of Gh0stRat using Volatility plugin
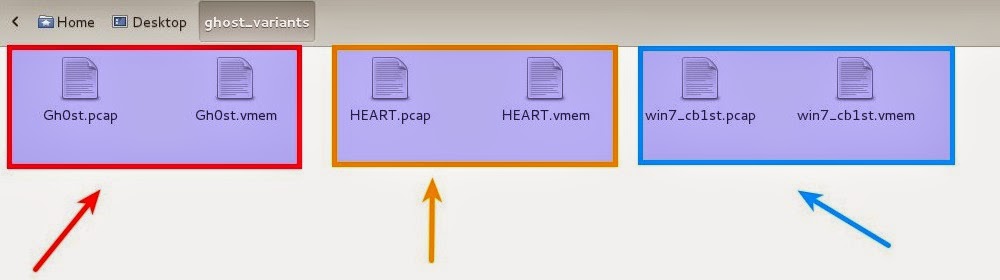
In order to demonstrate the capabilities of the plugin, I analyzed multiple variants of Gh0stRat samples in the sandbox and collected the pcap and the memory image. The below screenshot show the pcaps and the memory (.vmem files) images of three different Gh0stRat samples. The First two samples were run on Windows XP SP3 and third sample was run on Win7SP0x86
6.1. Investigating the first sample (Gh0st.vmem and Gh0st.pcap)
The below screenshot shows the Gh0stRat communication. In this case the infected host 192.168.1.100 (which is the Windows XP machine where the sample was run) is sending the encrypted traffic to C2 (192.168.1.2 which is my Linux machine acting as C2) on port 2011, also in this case the magic keyword "Gh0st" was sent in the first 5 bytes
To use the plugin just copy it to the Volatility plugins directory. After copying the plugin, the Volatility's plugin system will automatically register the plugin as shown below
6. Detecting and decrypting multiple variants of Gh0stRat using Volatility plugin
In order to demonstrate the capabilities of the plugin, I analyzed multiple variants of Gh0stRat samples in the sandbox and collected the pcap and the memory image. The below screenshot show the pcaps and the memory (.vmem files) images of three different Gh0stRat samples. The First two samples were run on Windows XP SP3 and third sample was run on Win7SP0x86
6.1. Investigating the first sample (Gh0st.vmem and Gh0st.pcap)
The below screenshot shows the Gh0stRat communication. In this case the infected host 192.168.1.100 (which is the Windows XP machine where the sample was run) is sending the encrypted traffic to C2 (192.168.1.2 which is my Linux machine acting as C2) on port 2011, also in this case the magic keyword "Gh0st" was sent in the first 5 bytes
After running the plugin against the memory image (Gh0st.vmem), it detected the encrypted traffic in the memory and decrypted it, it also detected malicious process as svchost.exe process (with pid 408).
In the Decrypted traffic shown below, the system information is passed to the command and control server. The value shown in blue (05 00 00 00) which should be read as 00 00 00 05 (because of the little endian) format is the major version of the operating system which is 5.
The value shown in green (01 00 00 00) should be read as 00 00 00 01 is the minor version of the Operating system which is 1. So looking at these two values we can tell which OS was infected. In this case it is 5.1 which is Windows XP
The values shown in yellow (28 0a 00 00) should be read as 00 00 0a 28 is the build number of the operating system which in decimal is 2600. This is the build number of windows XP.
From the decrypted communication it can be seen that the Service Pack (service pack 3) and the Hostname (in this case it is "myhostname") of the infected machine is also passed to the attacker
The Volatility plugin was able to automatically detect svchost.exe (with pid 408) as the malicious process, The plugin also detected malicious network communication associated with svchost.exe (with pid 408). The below screenshot also shows the connection to the IP 192.168.1.2 on port 2011( this is the same traffic captured in the pcap). This can help the investigators to quickly determine the C2 ip involved in the compromise.
svchost.exe is the legitimate OS process, and also the functionality of svchost.exe is to load DLL's running as service, so there is a possibility that svchost.exe loaded a malicious DLL. It's important from an incident response perspective to find the malicious DLL. Once the malicious process is identified, the plugin also lists all the DLL's loaded by the malicious process. This can help the investigators to quickly pin point on a malicious DLL. The below screenshot shows the suspicious file loaded by the svchost.exe (pid408).
After dumping this suspicious file from memory and submitting to VirusTotal, Antivirus vendors detect this as (Magania/Farfli) which is same as Gh0strat.
6.2. Investigating the second sample (HEART.vmem and HEART.pcap)
The below screenshot shows the Gh0stRat communication with 192.168.1.2 on port 2013, in this case the magic keyword "HEART" was sent in the first 5 bytes
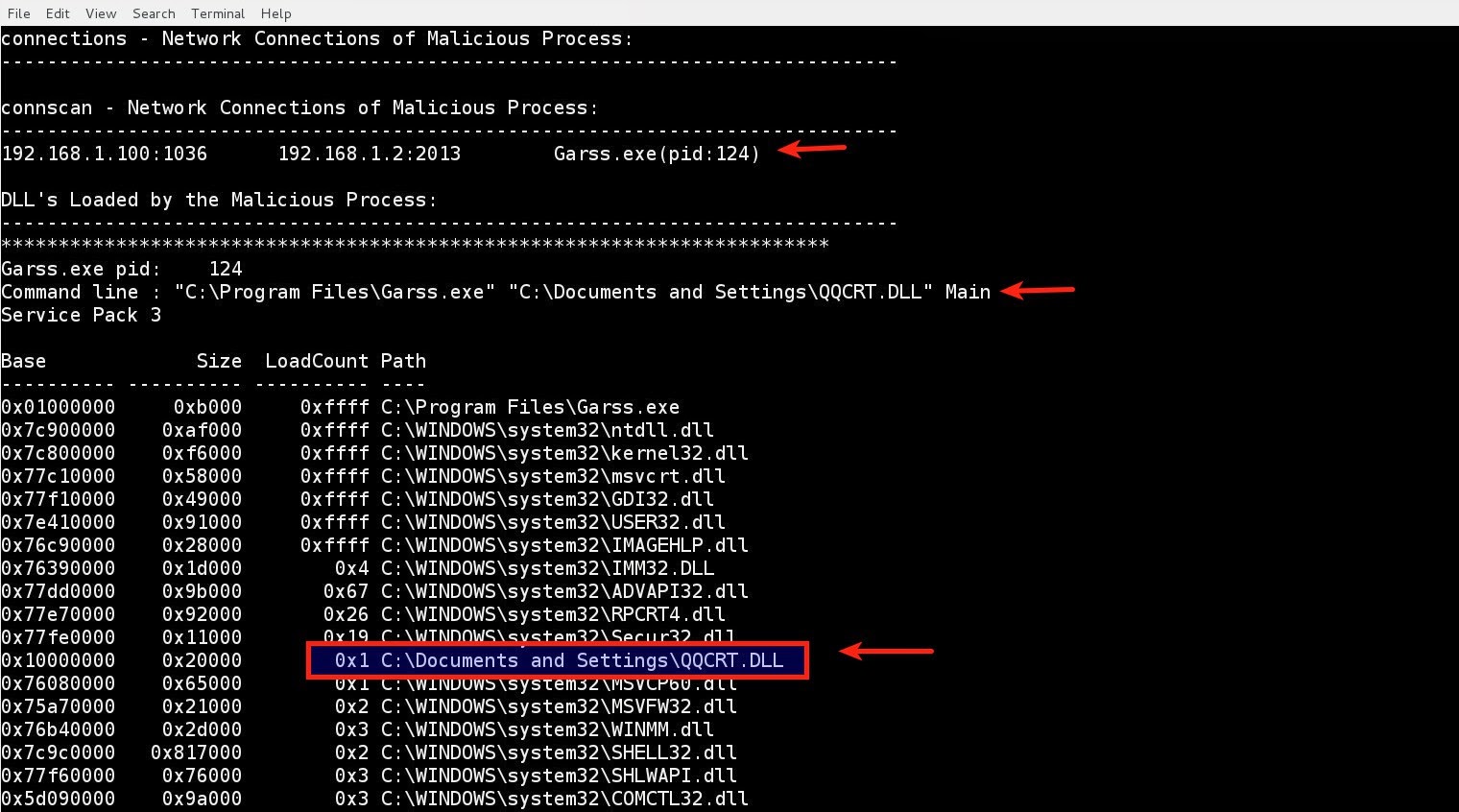
After running the plugin against the memory image (HEART.vmem), it detected the encrypted traffic in the memory and decrypted it, it also detected malicious process as Garss.exe process (with pid 124).
Plugin also detected the malicious communication to the IP 192.168.1.2 on port 2013 (that we saw in the pcap) which is associated with process Garss.exe (with pid 124). It also detected all the DLL's loaded by the malicious process. From the below screenshot it can be seen that a malicious DLL is loaded by the process(Garss.exe)
6.3. Investigating the Third sample - Windows7 image (win7_cb1st.vmem and win7_cb1st.pcap)
The below screenshot shows the Gh0stRat communication with 192.168.1.3 on port 8000, in this case the magic keyword "cb1st" was sent in the first 5 bytes
After running the plugin against the Windows 7 memory image (win7_cb1st.vmem), it detected the encrypted traffic in the memory and decrypted it, it also detected malicious process as svchost.exe process (with pid 840). Based on the major, minor version and the build number ((highlighted in blue, green and yellow) from the decrypted traffic it can be determined that the infected OS is Windows 7 and the hostname of the infected machine is "win7-sandbox"
Plugin also detected the malicious communication to the IP 192.168.1.3 on port 8000(that we saw in the pcap) which is associated with process svchost.exe (with pid 840).
The plugin also detected all the DLL's loaded by the malicious process. From the below screenshot it can be seen that a malicious DLL is loaded by the process(svchost.exe)
This blog post explained the details of Gh0stRat communication and showed the method to detect it manually using Volatility advanced memory forensics framework. I also presented a plugin that detects the malicious process, network communication, Loaded DLL's and decrypts the network communication of multiple variants of Gh0stRat in an automated way. This allows the incident responders/Investigators to quickly detect the malicious Gh0stRat artifacts, C2 ip and it also helps in determining the type of information that was exchanged between the infected host and the C2 server.
Thanks to core developers of Volatility for their encouragement, for being an inspiration and for authoring one of the best books i have read last year and many years to come "The Art of Memory Forensics": Michael Ligh (@iMHLv2), Andrew Case (@attrc), Jamie Levy (@gleeda) and Aaron Walters(@4tphi). Special thanks to Michael Ligh for going through my content and suggesting the changes (inspite of his busy schedule) and also for suggesting me to submit the plugin to the Volatility Plugin Contest 2014
728x90
'computer forensics' 카테고리의 다른 글
| Acquiring Linux Memory from a Server Far Far Away (0) | 2017.02.22 |
|---|---|
| DDos Syn 패킷 분석 (0) | 2016.01.18 |
| 네트워크 포렌식 (backdoor) (0) | 2015.12.29 |
| 네트워크 포렌식 문제 (0) | 2015.12.19 |
| The Pmem Memory acquisition suite. (0) | 2015.04.26 |