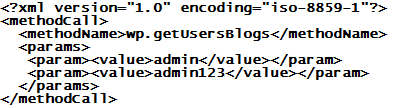
Now that the XMLRPC "pingback" DDoS problem in WordPress is increasingly under control, the crooks now seem to try brute force password guessing attacks via the "wp.getUsersBlogs" method of xmlrpc.php. ISC reader Robert sent in some logs that show a massive distributed (> 3000 source IPs) attempt at guessing passwords on his Wordpress installation. The requests look like the one shown below
and are posted into xmlrpc.php. Unfortunately, the web server responds with a 200-OK in all cases, because the post to xmlrpc.php actually WAS successful. The expected "403 - Not Authorized" error is part of the XML message that the server returns as payload. Hence, to determine what is going on, relying on simple HTTP web server logs is not sufficient. One of the problems with this is that "traditional" means of curbing brute force attacks in WordPress, like using BruteProtect, are less effective, because most of these add-ons tend to watch only wp_login.php and the associated wp_login_failed result, which does not trigger in the case of an xmlrpc login error.
If you are seeing similar attacks, and have found an effective way of thwarting them, please share in the comments below.
'malware ' 카테고리의 다른 글
| Analysis of a Win32 (Neutrino?)/n3nmtx Trojan (0) | 2014.07.27 |
|---|---|
| App "telemetry" (0) | 2014.07.23 |
| Keeping the RATs out: the trap is sprung - Part 3 (0) | 2014.07.21 |
| Is use-after-free exploitation dead? The new IE memory protector will tell you (0) | 2014.07.18 |
| Keeping the RATs out: **it happens - Part 2 (0) | 2014.07.18 |