728x90
SSL MiTM attack in AFNetworking 2.5.1 - Do NOT use it in production!
During a recent mobile application security analysis for one of our clients, we identified a quite unobvious behaviour in apps that use the AFNetworkinglibrary.
It turned out that because of a logic flaw in the latest version of the library, SSL MiTM attacks are feasible in apps using AFNetworking 2.5.1.
The issue occurs even when the mobile application requests the library to apply checks for server validation in SSL certificates.It turned out that because of a logic flaw in the latest version of the library, SSL MiTM attacks are feasible in apps using AFNetworking 2.5.1.
Given that AFNetworking library is one of the most popular networking library for iOS and OS X and it is used by Pinterest, Heroku and Simple among others, the problem could affect a very high number of mobile users.
Here's the usage of AFNetworking library on Github:
Although the vendor has been aware of this issue since February 13th, 2015, there's still no official patch for it.
| Github statistics for the AFNetworking library |
Although the vendor has been aware of this issue since February 13th, 2015, there's still no official patch for it.
The Issue
On the 6th of March, when looking at the tested application source code, we identified the following part:#if TARGET_IPHONE_SIMULATOR && defined(DEBUG) [AFSecurityPolicy setAllowInvalidCertificates:YES] #endif
SSL certificate validation was disabled if and only if the build target was the iPhone simulator and the DEBUG flag was set. Let's remind that the default value of the allowsInvalidSSLCertificate property is NO.
We tested the app on a real device and, unexpectedly, we found that all the SSL traffic could be regularly intercepted through a proxy like Burp without any intervention!
Further investigation led us to a particular part in AFNetworking code where trust evaluation was somehow disabled.
After few minutes, we figured out that there was a logical bug while evaluating trust for SSL certificate, whose consequence was to completely disable SSL certificate validation.
- (BOOL)evaluateServerTrust:(SecTrustRef)serverTrust forDomain:(NSString *)domain
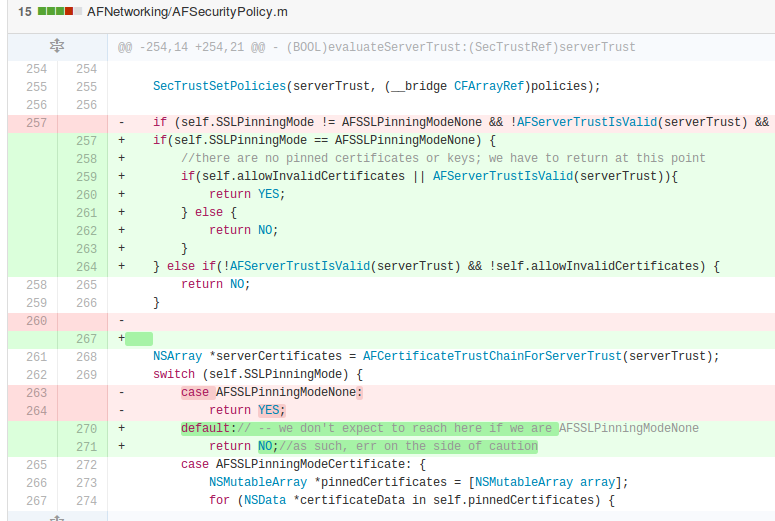
method within the AFSecurityPolicy.m file: - (BOOL)evaluateServerTrust:(SecTrustRef)serverTrust forDomain:(NSString *)domain { NSMutableArray *policies = [NSMutableArray array]; if (self.validatesDomainName) { [policies addObject:(__bridge_transfer id)SecPolicyCreateSSL(true, (__bridge CFStringRef)domain)]; } else { [policies addObject:(__bridge_transfer id)SecPolicyCreateBasicX509()]; } SecTrustSetPolicies(serverTrust, (__bridge CFArrayRef)policies); if (self.SSLPinningMode != AFSSLPinningModeNone && !AFServerTrustIsValid(serverTrust) && !self.allowInvalidCertificates) { return NO; } NSArray *serverCertificates = AFCertificateTrustChainForServerTrust(serverTrust); switch (self.SSLPinningMode) { case AFSSLPinningModeNone: return YES;
Which means that if pinning is not used,
SSLPinningMode == AFSSLPinningModeNone
then the yellow-highlighted `if` statement evaluates to `false`, even though the property `allowInvalidCertificates` is set to `NO`.
The code flow will hence reach the red-highlighted branch, with the result ofcancelling out the whole SSL certificate validation.
It is also important to note that the default value of SSLPinningMode is, indeed, `AFSSLPinningModeNone`.
After a few "feeling cool" moments, we discovered that the implementation flaw was already known and reported here. One month later a new issue was submitted with a more clear description.
Further investigation allowed us to understand that the bug was introduced in late January during the development of AFNetworking 2.5.1.
Warning: 2.5.1 is the latest version at the time of this writing and is installed by default using CocoaPods if not stated otherwise.
The impact: SSL MiTM attacks
Eventually, the overall risk can be evaluated as high since a MiTM attack is feasible in all iOS applications using AFNetworking 2.5.1, even though the developers were mindful enough to disable debug settings in the production build.
Moreover, take into consideration that mobile apps are typically used while being connected via public hotspots.
Moreover, take into consideration that mobile apps are typically used while being connected via public hotspots.
Remediation
Minded Security suggests to consider applying the patch proposed by duttskion his GitHub AFNetworking code, as a workaround until an official patch will be released (click to enlarge):Unofficial Patch of AFNetworking issue
Finally, it's worth mentioning that setting allowInvalidCertificates to YES would make you deliberately vulnerable no matter what the library does (yes, we know you know, but.. you know..;).
728x90
'Security_Study' 카테고리의 다른 글
| Exploiting weak randomness in web applications (0) | 2015.04.13 |
|---|---|
| Oracle SQL Injection Guides and Whitepapers (0) | 2015.04.11 |
| DDoS on UPNP Devices (0) | 2015.03.17 |
| No Wireshark? No TCPDump? No Problem! (0) | 2015.03.05 |
| Experimenting with Honeypots Using The Modern Honey Network (0) | 2015.02.21 |