The universe is full of "Black Energy" and so is cyberspace. Not so very long ago, we wrote about a sample of the BlackEnergy family discovered via VirusTotal. The family is allegedly the same malware used in the cyber-attack against Georgia in 2008. Last Friday, another fresh variant was submitted to VirusTotal. And this time it is more obvious on how it was being distributed: a zip file containing an executable. Again, as was the case earlier this month, the sample was submitted from Ukraine.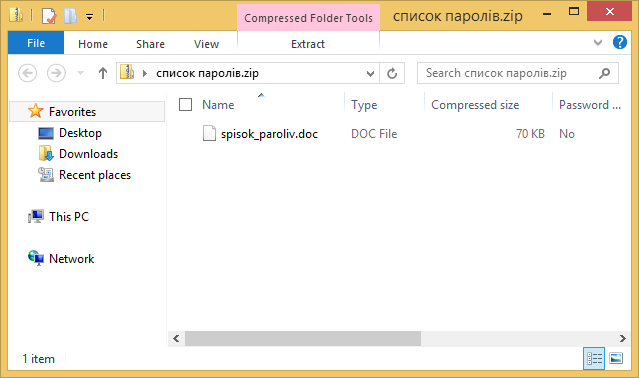
The filename of the zip file means "password list" spelled out in the Cyrillic alphabet. For the executable, it means the same but spelled out in the Latin alphabet. Take note that the executable has a .doc extension. It is not clear how the sample can be run by the victim. Our guess is that there might be a zip application used by the intended target which supports opening samples based on their true file type regardless of their extension. Of course it is also possible that the attackers just made a mistake.
Checking the instance of the executable in VirusTotal, it was submitted from Belgium just a few minutes earlier. Given the current situation in Ukraine, and that Belgium is the center of the European Union government (and where NATO Headquarters is located), we cannot discount the theory that they are related.
We think the sample is possibly sent as attachment in spear-phishing e-mails pretending to be IT advisories warning people to avoid certain passwords.
Unlike the earlier variant, the sample no longer uses a kernel mode component to inject the user mode DLL into svchost.exe. This time it just uses a user mode dropper to load the DLL via rundll32.exe. Ditching the kernel mode component might be an attempt to get around the driver signing enforcement protection found in modern Windows systems.
The user mode DLL has also been rewritten (timestamp of June 26, 2014) to support the change. It now has a different configuration format but still uses a C&C that falls under the same IP address block:
The dropper will also open a decoy document to hide its malicious activity:
Take note that there is no software vulnerability or exploit involved. The decoy document is created and opened by the dropper programmatically. This is something similar to what we have seen before in what might be the first documented APT attempt in OS X. The malware did however exempt its host process (rundll32.exe) from DEP, which may open up an attack surface for future exploitation:
Bottom line: if you're involved in European/Ukrainian diplomacy… beware BlackEnergy.
'malware ' 카테고리의 다른 글
| Targeted Attacks on French Company Exploit Multiple Word Vulnerabilities (0) | 2014.07.17 |
|---|---|
| Is use-after-free exploitation dead? The new IE memory protector will tell you (0) | 2014.07.17 |
| 표적 형 공격에 사용되는 "KIVARS": 새로운 64 비트 버전을 투입 (0) | 2014.07.07 |
| Isolated Heap for Internet Explorer Helps Mitigate UAF Exploits (0) | 2014.07.02 |
| 시작 시간이 설정된 RAT "PlugX"C & C 설정 다운로드에 Dropbox를 악용 (0) | 2014.06.29 |